Vpn network diagram private virtual architecture enterprise wireless utm using appliances remote access controller points overview Virtual private networks (vpn). computer and network examples Mpls network diagram vpn route within data sample changing attributes ipspace enterprise infrastructure deployment sent real approximated designed following
What is Hacking: Why you should use VPN | Top 5 reasons to use a VPN.
Vpn site architecture vpc network premises aws review connection multiple hybrid connected level high initial development state What is hacking: why you should use vpn Visio vpn
The basics of vpn explained
Vpn explanationVpn topology network dhcp sonicwall Vpn mustVpn 101 – vpnmentor’s vpn guide for newbies.
Vpn diagram vpnmentor mobile newbies guide use vpns deviceMeraki vpn site cisco diagram network duo client using set authentication easily mx radius technology configure 2021 How to secure your internet with a vpn (infographic) 2024How to fix a slow network while using a vpn.

Vpn – it network consulting
Vpn network server virtual private works explained proxy computing firewall secure ip internet gif basics multipoint faq find know vsThe ultimate vpn guide: technical and use case explanation of the most Network private virtual networks vpn examples enterprise computer diagram symbols clipart networking cliparts remote example create site diagrams drawing securityVpn works tunnel vpns network internet infographic security virtual personal private privacy two connection via depiction simplified.
Vpn passthroughVpn vpns site access remote connections use What is vpn passthroughAn overview of enterprise vpn.

Visio vpn
Vpns: your personal tunnel to privacyUseful answers Types of vpnsReview site-to-site vpn architecture :: get started with aws for.
Vpn vpns pptp connections cisco anyconnect postpaidHow do vpns work? vpn encryption & tunneling explained Setting up vpns easily with cipeVirtual private network (vpn).

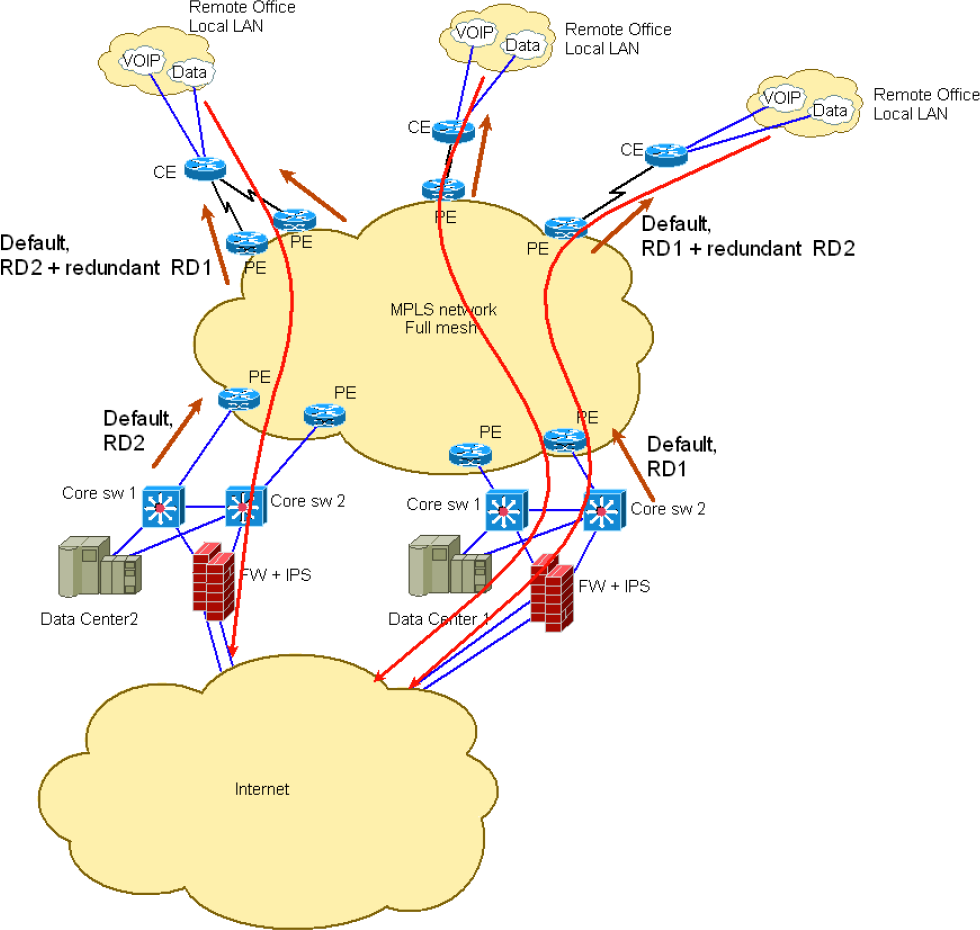
Changing vpnv4 route attributes within the mpls/vpn network « ipspace
Vpn vpns encryption traffic encrypted tunneling explained encryptVpn netburner typical Vpn network sanOpenvpn vpn debian buster linux.
Vpn works connectivity network diagram office campus ip internet hacking using off useVpn diagram network simple Vpn vpns extend cyberhootWhat is vpn (virtual private network)?.

Dhcp archives
Site-to-site vpn complexityVpn connection firewall entities hack malicious trying How to easily set up a site-to-site vpn using cisco merakiAll about vpns « tiptopsecurity.
Vpn diagram architecture using showing help looksWhat is a vpn, and how can it help you?- the mac observer Vpn site cisco s2s complexity community problem too sites.

Virtual private networks (VPN). Computer and Network Examples

Virtual Private Network (VPN) - NETWORK ENCYCLOPEDIA

OpenVPN | How To Set Up OpenVPN server on Debian 10 Buster

How Do VPNs Work? VPN Encryption & Tunneling Explained

What is Hacking: Why you should use VPN | Top 5 reasons to use a VPN.

How to Secure Your Internet With a VPN (Infographic) 2024 | Begindot

vpn – IT Network Consulting | Design, Deploy and Support | San Diego